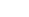"High security solution group"
IRIENCE
Experience the segmented and specialized iris recognition technology of IRIENCE along with our iris recognition algorithm and software developers. IRIENCE, truly the best iris algorithm company in Korea, who complies with international standards and maintains a strict operation offers a world class level iris recognition technology to our users.
Access control
· Problems by using logical security (ID/PWD, OTP, RFID, security card, etc.)
· Security problems of stealing other’s ID/PWD and an implied use.
· Risk of hacking attempt by using a predictable PWD (1 minute to decrypt an 8-digit text)
· Inconvenience by possessing media including OTP, RFID, security card and risk of loss
· Requires a complex PWD or a periodic PWD change
· Implement physical security by iris authentication(authentication without media, Bio-PWD)
· Prepare for hacking by distributed management of iris information, construct iris information to be non-reusable
· Build up a safe and reliable security access control system when accessing the DB and system
| Logical Security Technology | Physical Security Technology | |||
| Password | OTP | Fingerprint recognition | Iris recognition | |
| Recognition data |  |
 |
 |
 |
| Media | Combination of letters, numbers, and symbols | Random number | Finger curve | Pattern of iris |
|---|---|---|---|---|
| Possibility of theft | High | Low | Possibility | impossibility |
| Technical level | Low | General purpose technology | General purpose technology | High |
| Maintenance costs | Low | High | Low | Low |
| Security | Can be stolen and used implicitly 10-digit text decryption time 1 hour |
Risk of loss Replace every 2 years |
Risk of gastric alteration High Misperception |
physical Security the highest level of perception |
| Comparison | Limits of Logical Security Periodic replacement required Requires several combinations such as symbols |
High maintenance costs Always carry product Disable in case of emergency |
Contact biometric authentication 1:N method limit present |
non-Media authentication Most Confident Authentication |
Advanced Case Study On The Application of Iris Recognition
-
United States Army

Unmanned weapons system (Drones, unmanned combat vehicles, etc.)
Use iris for operator authentication -
NATO

Smart Helmet for Battlefield Information
User authentication(BAE system) -
Woori Bank

Woori Bank DB Access Control
Establishment of Bio(Iris) Recognition System
DB Access Control Iris Recognition Distributed Management System( Apply to 00 Bank)- Registration Structure
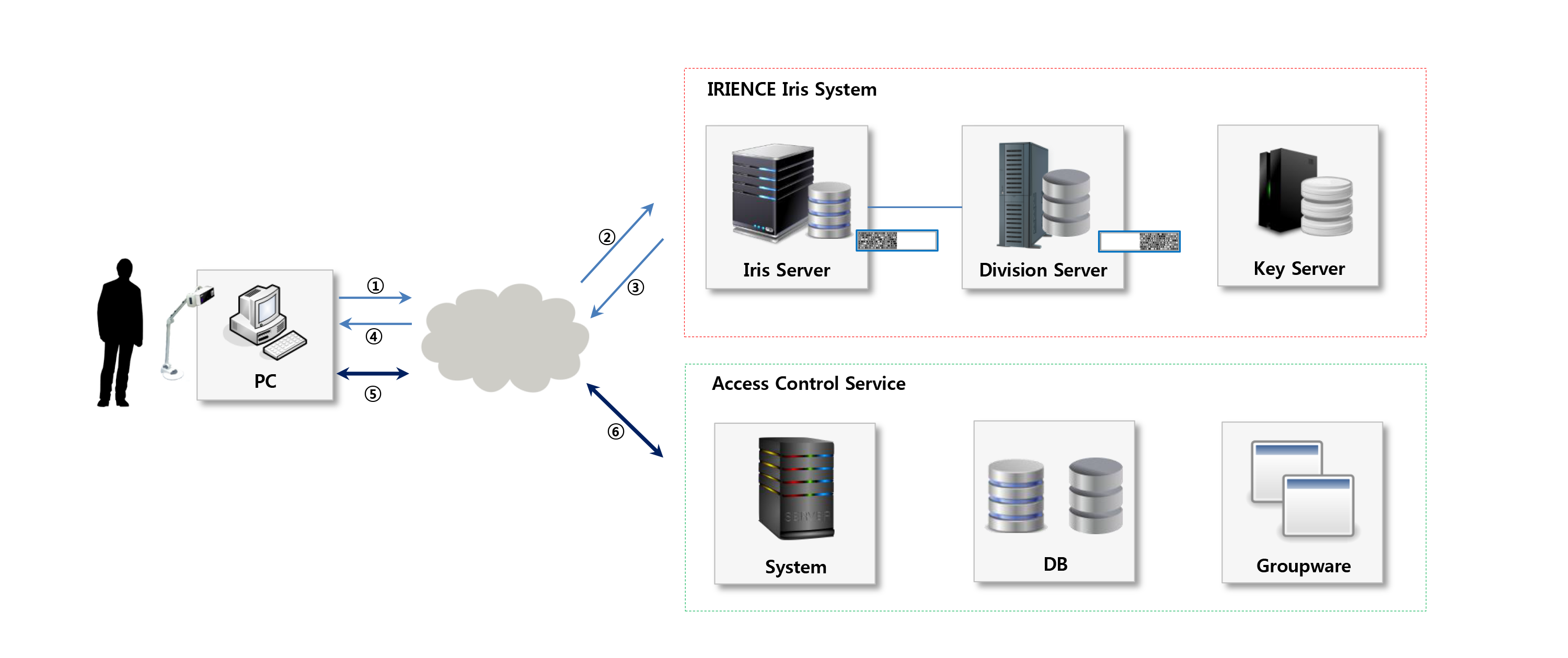
Installation Configuration of The Access Control Equipment
· Communication between the iris management server and terminal using TCP/IP
· Maximum number of 50,000 people which can be saved in the iris recognition device
· Use after registering iris on the terminal, and allowing user GATE in the server
· GATE access control by individual, access control available based on time/day of week
· Real-time monitoring support
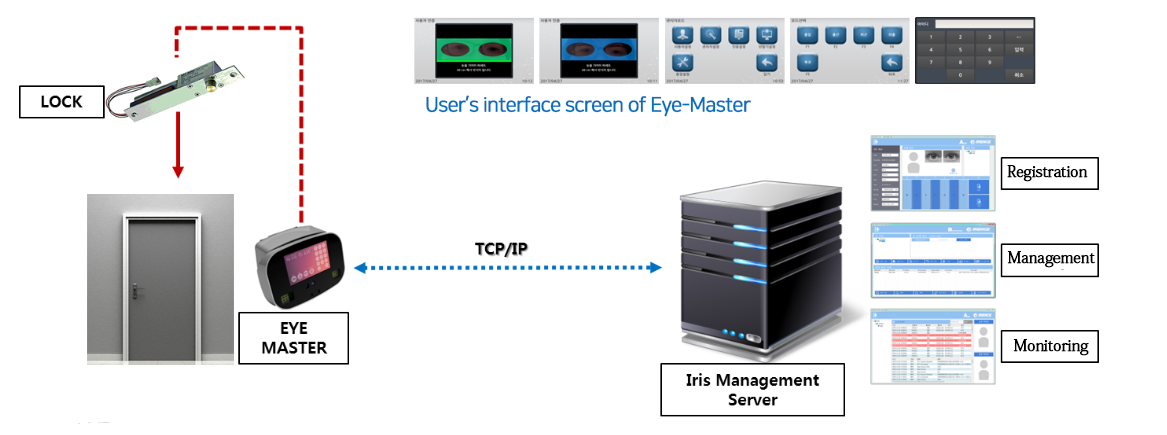
Access Control Network Configuration Diagram
· Communication between the iris management server and terminal using TCP/IP
· Gate door access control management by group(building/floor)
· Control gate door can be extended using the internet
· Capable of remote updates on terminals
Construction Site Access Control and Absenteeism Management System Configuration
Basic scheme(Local)

App for Control of Access and Absence in Construction Site
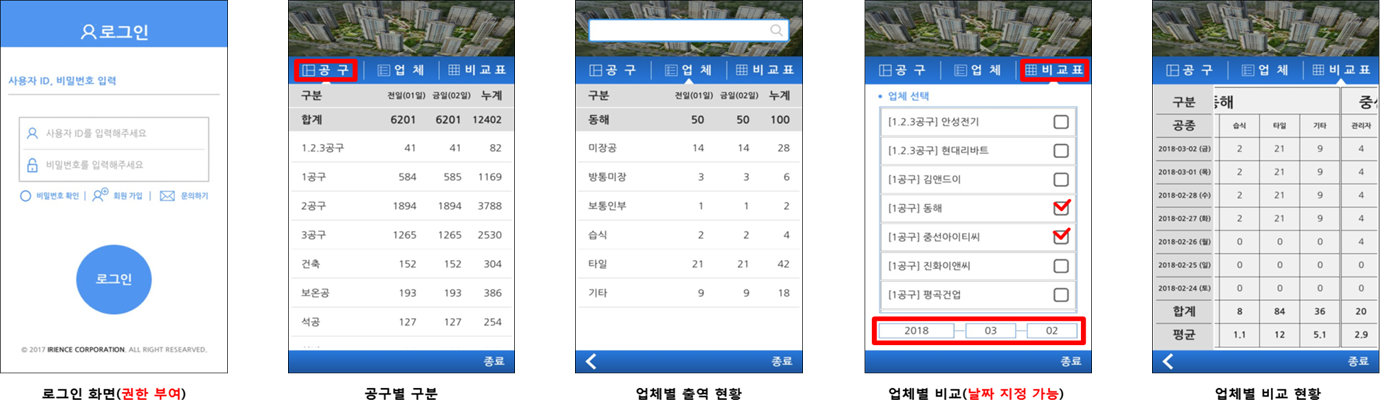
Major Characteristic of Access Control and Punctuality Management at A Construction Site
· Fast within a second and simple, accurate authentication
· Block access of an unauthorized person at the site (In case a tripod gate is installed)
· Robust authentication regardless of the surrounding environment and individual status
· Adoption of fraud preventing components
Preventing fake resident registration number, dual registration of resident registration numbers, duplicated registration of staff number, dual registration of iris
· Capable of commute authentication without internet
· Low maintenance cost compared to other operation
· Finding ways to eradicate delayed payment of wage for construction workforce and protection of field staffs’ right
Preventing duplicated payment of labor cost in case a dispute between the contractor and field staffs occur due to delayed payment of wage
Increased protection of workers’ right
Characteristic of distributed management of iris information
· Split iris information and save at a physically different space(preparing for external hacking attempts)
· Manage in various ways by combining the splitting method and splitting ratio, etc.
· Impossible to reproduce the original information by using a different encryption key during transmission, save, generating, DB, respectively
· Used in the financial sector where a high level of security is required
· Can be used regardless of the type of terminals, approach, service due to its server storage mechanism
Offline Payment System Without Cash or Credit card
Iris Authentication System for Identification (Applying to a health clinic)
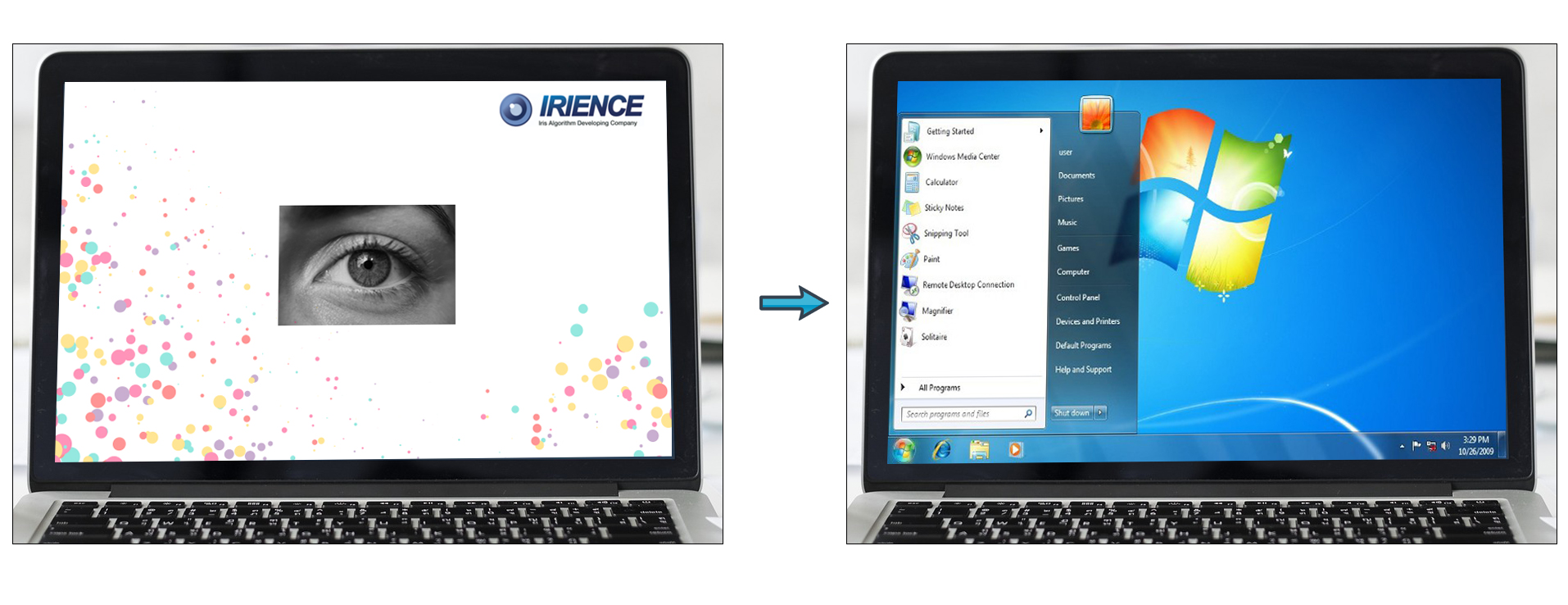
PC Login and Folder Security
PC login
Folder security
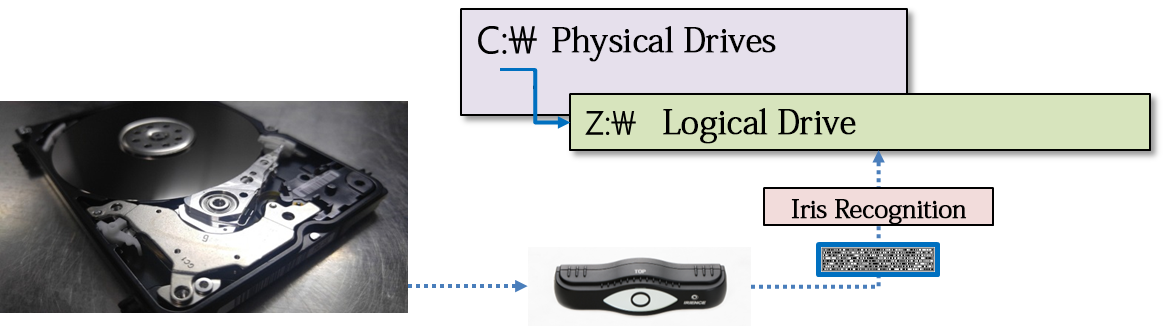
Securing Iris Authentication Documents
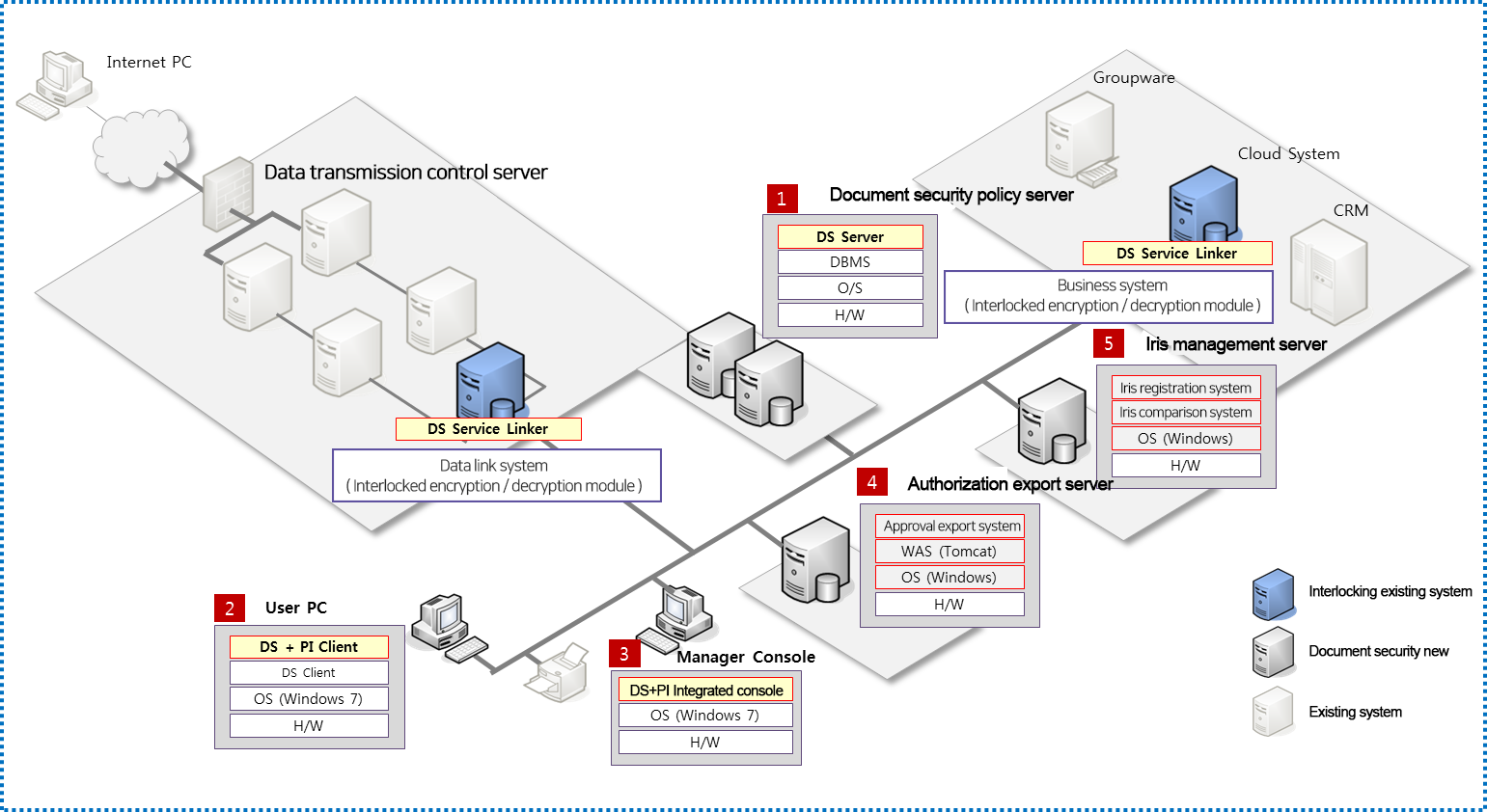
Immigration Inspection Using Iris Recognition
· Entrance of foreign passengers / departure of domestic passengers : automatic immigration inspection through iris recognition, capable of safe and rapid check-in
· Airport staff : install an iris recognition access controller at restricted areas and important facilities which require high level security
Iris authentication immigration procedure
Passport presentation
Iris scan
Audit
Data storage
Entry/Exit
Airport immigration system

Iris Registration Center

Passport reader

Square
(a iris-recognition device)
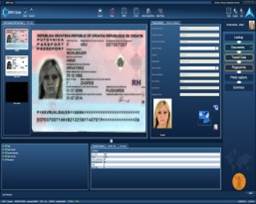
Immigration program

Automated immigration review